NewStarCTF WP WEEK4 _ reverse
茶
这题目主要是思路是字节码 MV 我们开始动调 主要目标进入 MV 做对齐 ,TEA
对其关键代码进行分析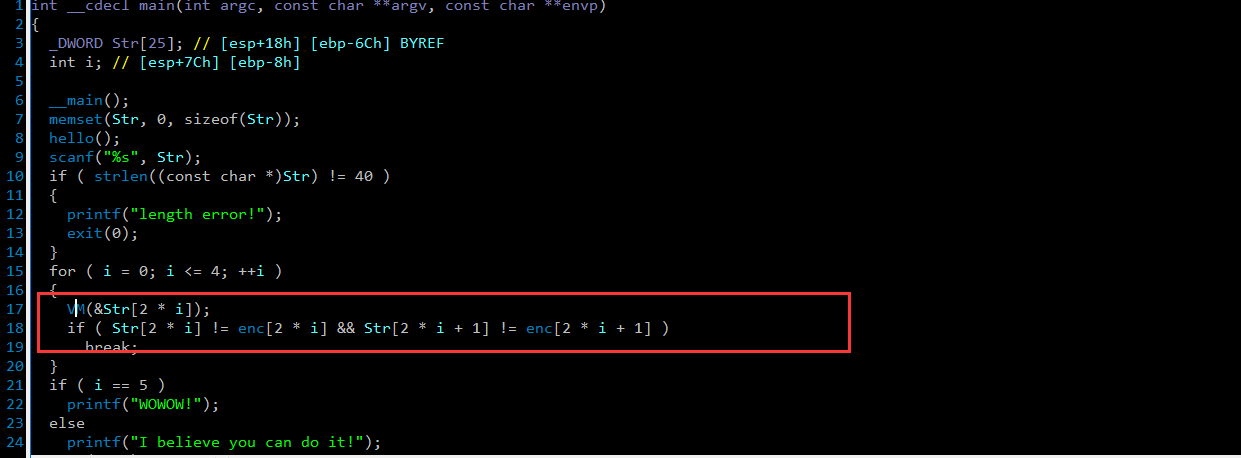
跟进VM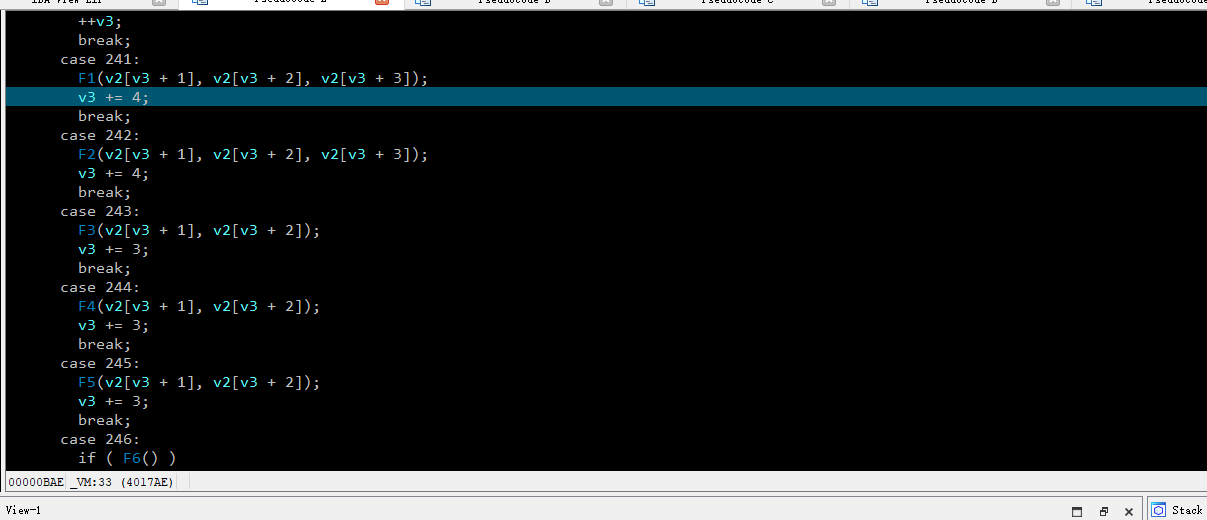
分析 一共是case 5次 长度为40 opencode 静态也找不到需要的 我们进行动调 在vm出断点 f9 f7 进入 call 跳转 进入 vm public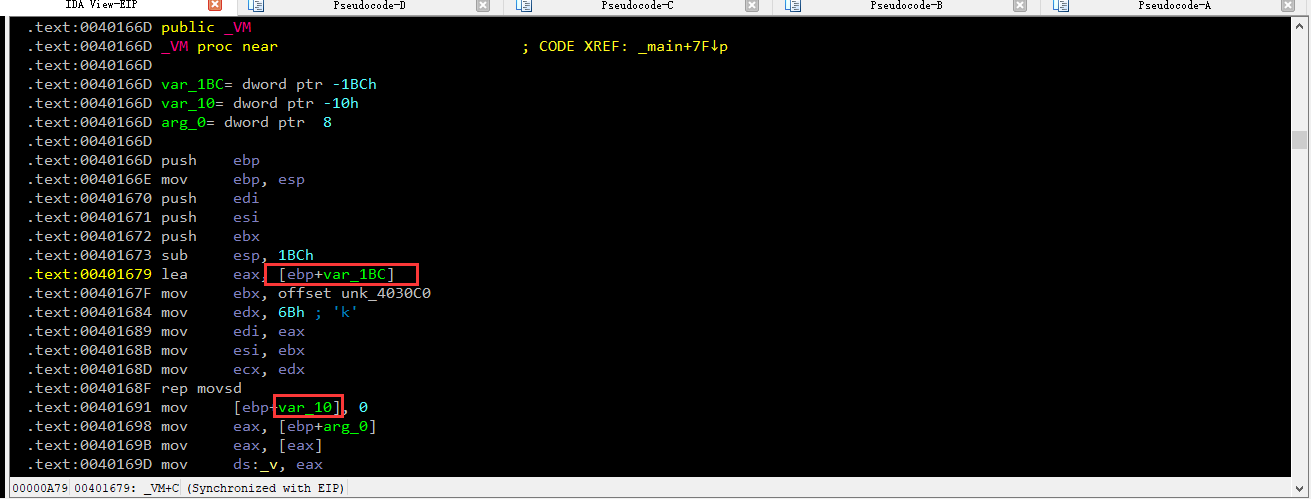
更近他们 var_10 栈 列表 一步一步对其
我们需要从下往上写 堆栈的原理的 先入栈的会在栈底
1 | 0xF1[0,0,2] |
后面数值 在K 和 enc 可以找到
1 |
|
简单的跨栏
apk 反编译 是一段RC4 加密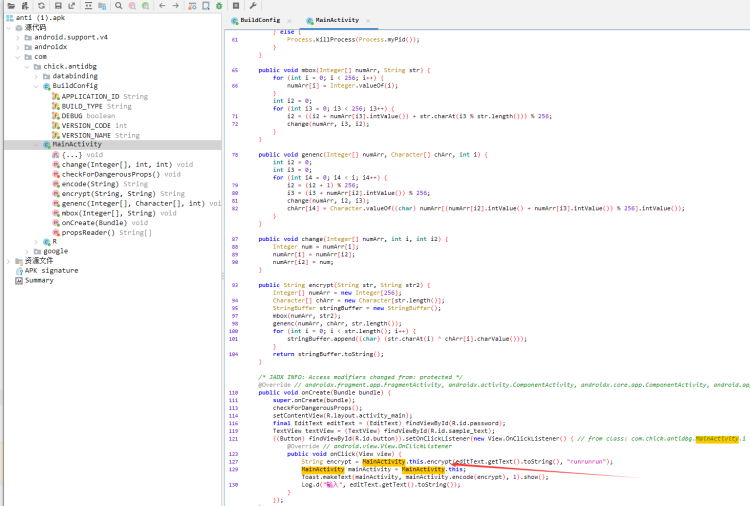
点encode是native函数,将lib中的libantidbg.so提取 丢ida 看看 变表base64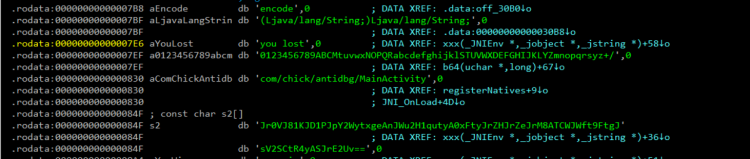
base64 解码 转hex 替换参数
写RC4
1 | #include<bits/stdc++.h> |
js
丢工具反一下
1 | function _0x4a2285(_0x2b5a00) { |
base64解码转hex
js在线穿他 admin 和 123456
对原脚本修改
1 | #include<bits/stdc++.h> |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 L1Nk8ug's Blog!