NewStarCTF WP WEEK3 _ reverse
花
ida 丢进去 脱花 跟下 RC4判断一下 密钥 一串wowo…..
1 |
|
STL
跑v7
1 |
|
带入v7 跑v13
1 | v7 =[1359286798,84564308,592899,404707156,408356433,22873420,1398229781,35407879,1426413319,471422726,1711934726] |
EzDLL
main往上走的几个函数 可以看到调用了TLSCallback 函数 跑路跑路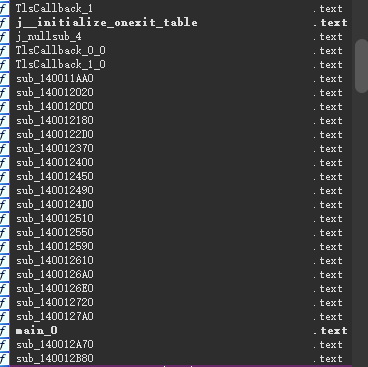
尝试跟进1_0试试 XTEA逆向 反编译 跟入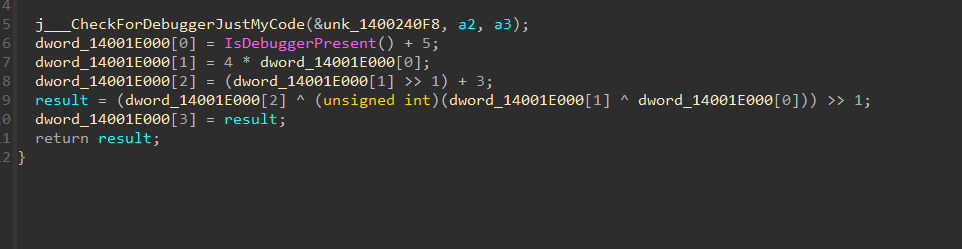
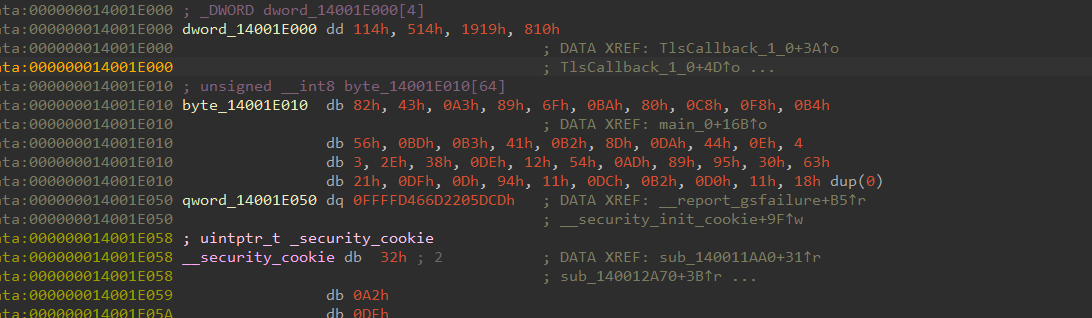
1 | #include<stdio.h> |
ez_chal
第一次用ida 调试 先开始静态分析 这边判断的是 输入32个值 也就是 要进到循环 得要过这个判断 。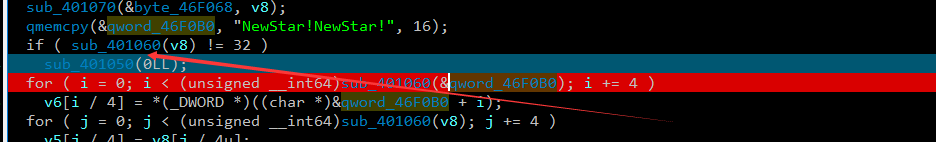
动态开始从路口函数开跑 在第一个指出进到输入往下 进入写 在第二个指出call 进行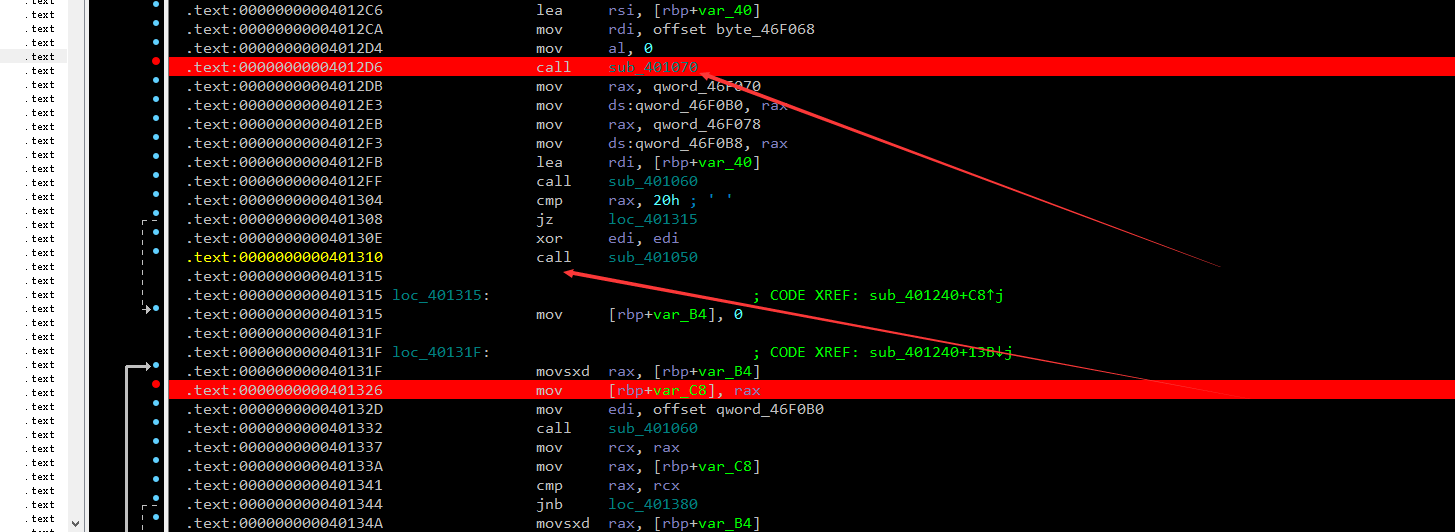
尝试 大于 32 和 小于 32可以绕过 在这个call f5反编译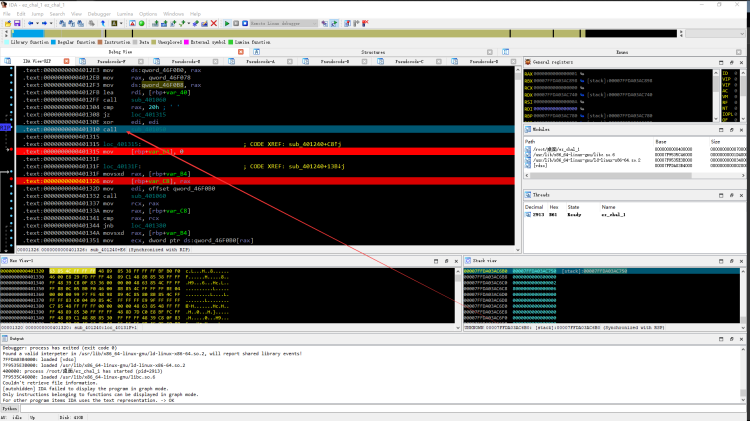
跟进 qword_46F0B0 十进制 转 字符串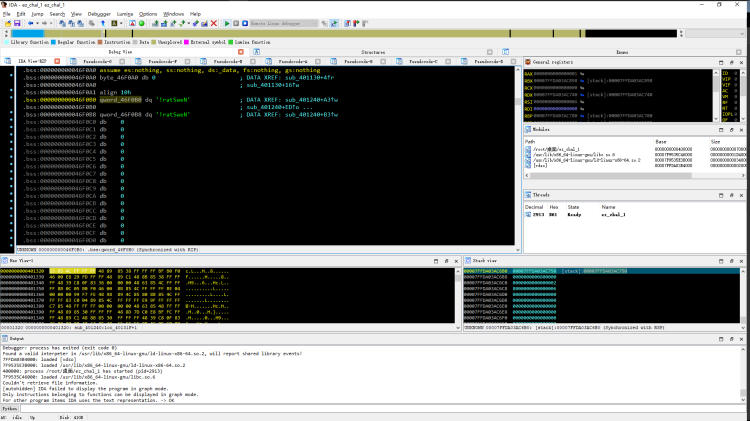
1 | char a[40]={0}; |
满足jz 就是等于32位值 进行跳转到加密 走到下一个 jz 也就是v6的比较断点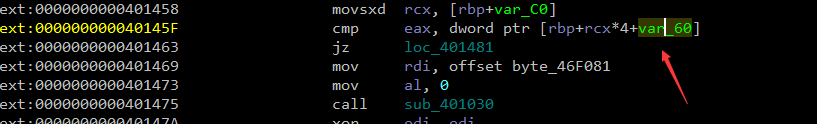
var_60更近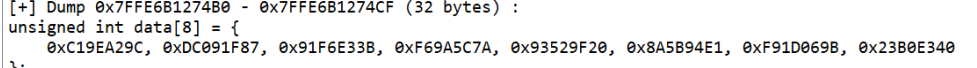
这是自己的
1 |
|
这是官方
1 |
|
Let’s Go
go 的语言在调用 main_main 之前要先调用main_init ! ! !这道题就是在mian_init
继续尝试往后面进行审计看看 是CBC算法加密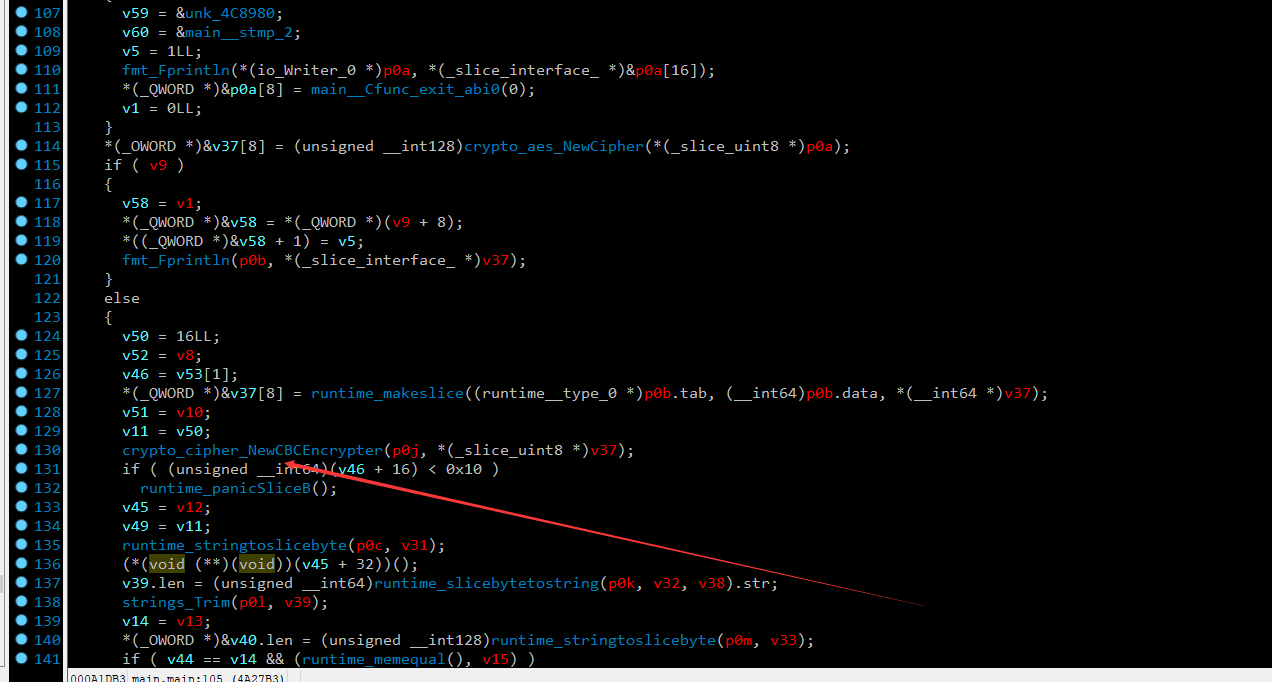
开始动调把断点设置在 crypto_aes_NewCipher 进行动调输入
main_init 的 32个值 call跳转进去点 进rax 的赋值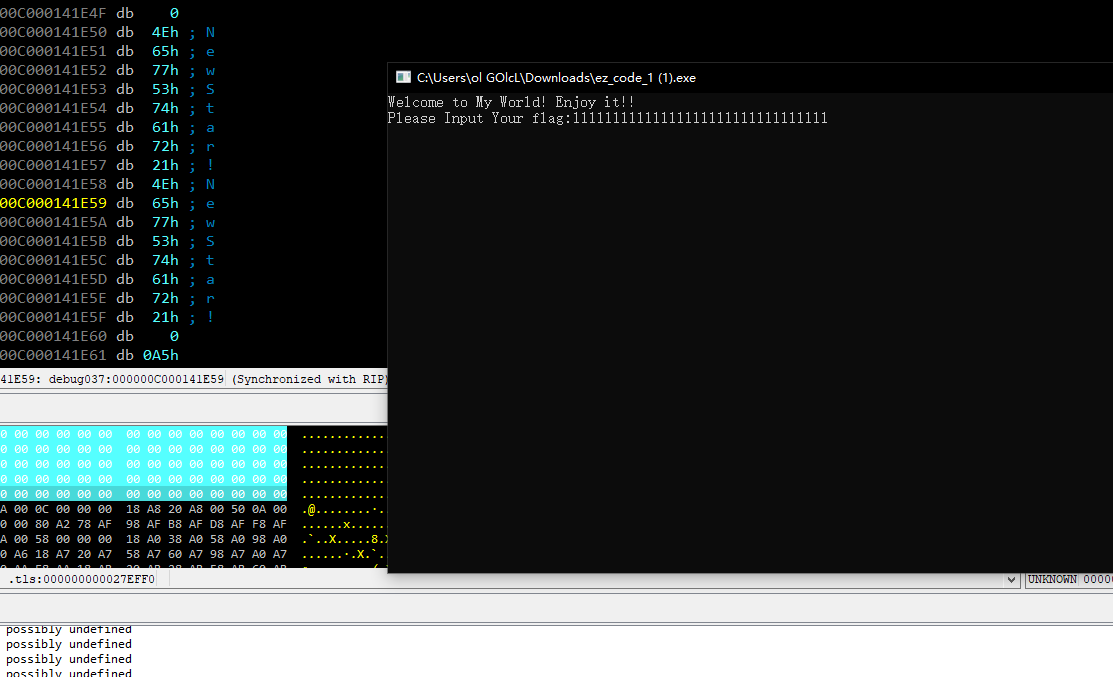
说明key就是NewStar!NewStar 还要一个 iv值分析堆栈汇编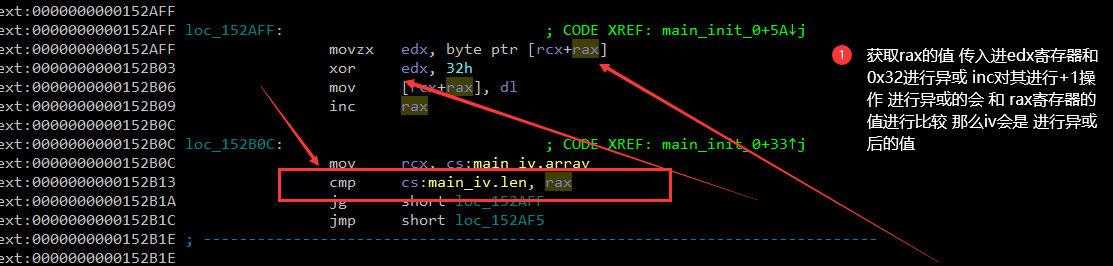
1 | s= 'NewStar!NewStar!' |
iv值是 0x7c 0x57 0x45 0x61 0x46 0x53 0x40 0x13 0x7c 0x57 0x45 0x61 0x46 0x53 0x40 0x13
得到 iv key 密文
1 | from Crypto.Cipher import AES |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 L1Nk8ug's Blog!